Software supply chain attacks have become one of the most serious and fastest-growing cyber threats facing organizations today. Instead of attacking a company directly, threat actors compromise trusted software, tools, or third-party components, turning routine updates, libraries, and services into hidden attack vectors.
This approach is especially effective because modern software is rarely built from scratch. Most applications rely on open-source libraries, CI/CD pipelines, cloud services, and external vendors. Once attackers infiltrate any part of this chain, malicious code can quietly spread to thousands, or even millions, of downstream users.
According to Gartner, 45% of organizations worldwide will have experienced a software supply chain attack by 2025. These incidents are often hard to detect, difficult to attribute, and typically discovered long after attackers have gained persistent access.
Understanding the different types of software supply chain attacks is a critical first step in reducing third-party cyber risk and strengthening organizational defenses.
What Are Software Supply Chain Attacks?
Software supply chain attacks occur when attackers compromise a trusted component within the software development or delivery process in order to infiltrate downstream targets. Rather than breaching an organization directly, threat actors exploit the trust placed in vendors, development tools, updates, or third-party dependencies.
These attacks take advantage of the interconnected nature of modern software ecosystems. A single compromised library, build system, or update server can impact hundreds or thousands of organizations at once, often without triggering traditional security alerts.
At a high level, a software supply chain attack targets any stage of the software lifecycle, including:
- Source code repositories
- Third-party libraries and packages
- Build and CI/CD pipelines
- Software update mechanisms
- Code-signing processes
Because these components are considered trusted by default, malicious activity can remain undetected for extended periods.
Why Software Supply Chain Attacks Are So Dangerous
Software supply chain attacks are uniquely dangerous because they exploit trust rather than technical weaknesses alone. When malicious code enters an environment through a trusted vendor, tool, or update, it often bypasses traditional security controls entirely.
Unlike opportunistic attacks, supply chain attacks are deliberate, targeted, and designed for long-term impact.
Key Reasons These Attacks Are So Effective
1. Inherited Trust
Organizations inherently trust:
- Signed software updates
- Well-known vendors
- Popular open-source libraries
Once a trusted component is compromised, malicious code is treated as legitimate, allowing attackers to move freely within environments.
2. Massive Blast Radius
A single compromised dependency or tool can impact:
- Thousands of companies
- Entire industries
- Critical infrastructure
This scalability makes supply chain attacks far more efficient than attacking organizations one by one.
3. Stealth and Long Dwell Time
Supply chain malware often:
- Avoids triggering security alerts
- Blends into normal application behavior
- Persists for months before detection
By the time an attack is discovered, attackers may already have exfiltrated data or established backdoors.
4. Difficult Attribution and Remediation
Identifying the root cause of a supply chain attack is challenging. Organizations must:
- Trace affected dependencies
- Coordinate with vendors
- Patch systems without breaking functionality
This slows incident response and increases operational risk.
The Most Common Types of Software Supply Chain Attacks
Software supply chain attacks take many forms, but they all share a common goal: compromising trusted components to reach downstream victims at scale. Below are the most common types of software supply chain attacks organizations should understand and monitor.
Upstream Supply Chain Attacks
Upstream attacks are the most common type of software supply chain attack. They occur when attackers compromise systems positioned “upstream” from end users—such as code repositories, vendor infrastructure, or update servers.
In these attacks, malicious code is injected directly into the software before it is distributed.
How upstream attacks work:
- A trusted repository or vendor system is compromised
- Malicious code is inserted into the source or update
- The poisoned software is distributed to downstream users
Because the software appears legitimate, victims unknowingly install malware through routine updates.
Midstream Supply Chain Attacks
Midstream attacks target intermediary systems rather than the original codebase itself. These include development tools, build servers, and deployment environments.
Attackers focus on tools used to assemble, test, or package software.
Common midstream targets include:
- Build servers
- Artifact repositories
- Testing frameworks
- Deployment automation tools
By compromising these systems, attackers can alter software without touching the original source code.
Compromised Software Dependencies
Modern applications rely heavily on third-party and open-source dependencies. When one of these dependencies is compromised, every application using it inherits the risk.
This creates a domino effect, where a single breach impacts thousands of downstream applications.
Types of dependencies at risk:
- Open-source libraries
- Frameworks
- Container base images
- SDKs and plugins
Without proper software composition analysis (SCA), these threats often go unnoticed.
Dependency Confusion Attacks
Dependency confusion attacks exploit how package managers resolve dependencies. Attackers publish malicious packages with the same name as internal libraries on public repositories.
When systems prioritize public repositories over private ones, the malicious package is downloaded instead.
Key characteristics:
- Targets CI/CD pipelines and automated builds
- Exploits naming conflicts
- Proven effective even in large enterprises
Package Typosquatting Attacks
Package typosquatting is a variation of dependency-based attacks that relies on human error.
Attackers upload malicious packages with names that closely resemble popular libraries, such as:
- Misspellings
- Character substitutions
- Extra or missing letters
Developers who mistype a package name may unknowingly install malicious code.
Code-Signing Certificate Attacks
Code-signing certificates are designed to verify software authenticity. In these attacks, threat actors compromise development environments and use legitimate certificates to sign malicious software.
This allows malware to:
- Appear authentic
- Bypass security controls
- Evade detection
These attacks often rely on social engineering or credential theft to access signing infrastructure.
CI/CD Infrastructure Attacks
CI/CD pipelines are a prime target because they control what code reaches production.
Attackers who compromise these pipelines can:
- Inject backdoors
- Modify application logic
- Insert crypto miners or spyware
A well-known example is the Codecov breach, where attackers compromised a CI/CD tool and gained access to thousands of customer environments.
Build Tooling and Configuration Attacks
As organizations adopt “everything as code,” insecure configuration files introduce new risks.
Common issues include:
- Poorly secured YAML files
- Exposed secrets in build configs
- Tampered automation scripts
These attacks are difficult to detect and can give attackers full control over application behavior.
Compromised Source Control Systems
Source control platforms are another high-value target. Attackers aim to gain privileged access through:
- Stolen credentials
- Excessive permissions
- Exposed secrets in repositories
Once inside, malicious code can be introduced and missed during code reviews—especially in fast-moving teams.
How Software Supply Chain Attacks Typically Work (Attack Flow)
While software supply chain attacks vary in technique, most follow a similar attack lifecycle. Understanding this flow helps security teams identify weak points and detect attacks earlier.
Below is a simplified breakdown of how these attacks typically unfold.
1. Reconnaissance
Attackers begin by identifying:
- Popular software vendors
- Widely used open-source projects
- CI/CD tools with broad adoption
The goal is to find a component that, if compromised, provides maximum downstream access.
2. Initial Compromise
Threat actors gain access through:
- Stolen or phished credentials
- Exploiting vulnerabilities in development tools
- Misconfigured repositories or build systems
High-privilege access is critical at this stage.
3. Payload Injection
Once inside, attackers insert malicious code into:
- Source repositories
- Build scripts
- Dependencies
- Update packages
This code is often designed to remain stealthy and evade detection.
4. Distribution to Downstream Victims
The compromised component is distributed through:
- Software updates
- Package repositories
- Automated CI/CD pipelines
Victims unknowingly install the malicious software as part of normal operations.
5. Post-Compromise Activity
After deployment, attackers may:
- Establish persistence
- Exfiltrate data
- Deploy additional malware
- Use access for espionage or lateral movement
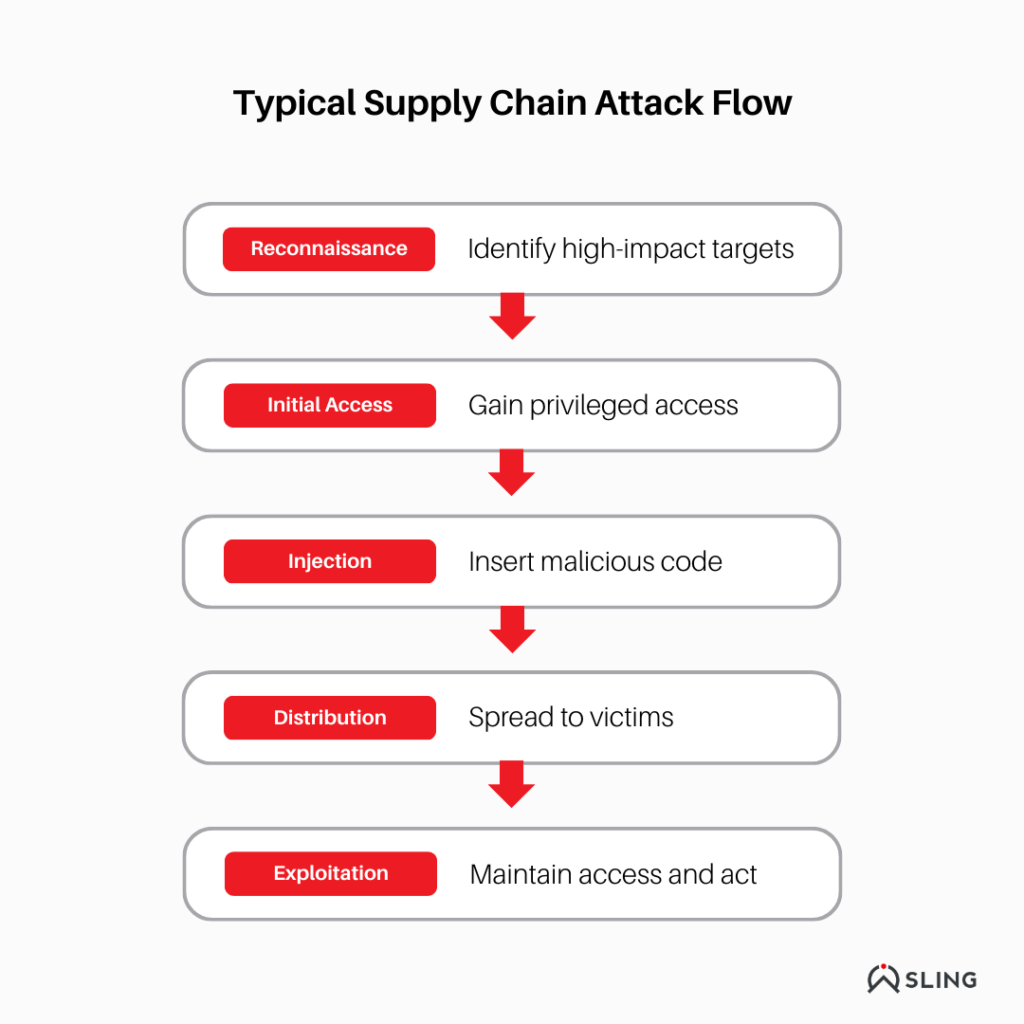
Because each stage blends into normal workflows, detection is often delayed—sometimes by months.
Who Is Most at Risk?
While software supply chain attacks can impact any organization, risk increases with dependency complexity and vendor exposure. Organizations that rely heavily on third-party software, automation, and shared infrastructure face the greatest threat.
Highest-Risk Groups
- Enterprises
Large organizations depend on numerous vendors and tools, making it difficult to maintain visibility across the entire software supply chain. - Software Vendors and SaaS Providers
As upstream suppliers, compromised vendors can unintentionally distribute malicious code to all customers. - Managed Security Service Providers (MSSPs)
A single breach can cascade across multiple client environments, amplifying impact. - Open-Source–Heavy Organizations
Poorly maintained or unknown dependencies increase exposure to hidden vulnerabilities. - Regulated and Critical Industries
Healthcare, finance, government, and energy sectors face higher operational and regulatory consequences.
Key Risk Factors
| Risk Factor | Impact |
| Extensive third-party use | Larger attack surface |
| Automated CI/CD pipelines | Faster spread of malware |
| Limited dependency visibility | Delayed detection |
| High trust in updates | Easier exploitation |
As software ecosystems grow more interconnected, nearly every organization becomes a potential downstream target of software supply chain attacks.
Key Indicators of a Software Supply Chain Attack
Detecting software supply chain attacks is challenging because malicious activity often blends into normal development and update processes. However, certain warning signs can indicate that a trusted component has been compromised.
Common Indicators to Watch For
- Unexpected dependency changes
New libraries, versions, or packages appearing without clear justification. - Unusual package versions or sources
Dependencies pulled from public repositories instead of internal ones. - Anomalous CI/CD behavior
Builds running unexpected scripts or producing unfamiliar artifacts. - Unsigned or altered updates
Missing, invalid, or changed code-signing certificates. - Suspicious outbound connections
Applications communicating with unfamiliar external domains after updates.
Why These Indicators Are Often Missed
Supply chain attacks exploit trusted workflows, meaning:
- Security tools may whitelist affected components
- Changes appear legitimate during reviews
- Alerts are dismissed as false positives
Identifying these signals early can significantly reduce dwell time and limit the impact of a software supply chain attack.
How to Reduce the Risk of Software Supply Chain Attacks
Reducing the risk of software supply chain attacks requires a shift from traditional perimeter-based security to full lifecycle visibility. Organizations must understand which third-party components, dependencies, and tools are embedded in their software and continuously monitor them for change. Maintaining accurate dependency inventories, validating update sources, and watching for unexpected version changes are critical first steps.
CI/CD pipelines also need strong protection, as they control what reaches production. Limiting access privileges, securing credentials, and monitoring build behavior can prevent attackers from injecting malicious code unnoticed. Equally important is verifying software integrity by validating code-signing certificates and detecting unauthorized modifications.
Finally, third-party risk management should be continuous rather than point-in-time. Monitoring externally exposed assets linked to vendors helps organizations identify new attack paths early, reducing dwell time and limiting the impact of a supply chain compromise.
The Role of Third-Party Risk Management in Supply Chain Security
Effective defense against software supply chain attacks depends heavily on strong third-party risk management (TPRM). Because these attacks often originate outside an organization’s direct control, visibility into vendors and external dependencies is essential.
Traditional TPRM programs rely on periodic questionnaires and self-attestations, which provide only a snapshot in time. In reality, vendor environments change constantly, new assets are deployed, configurations shift, and vulnerabilities emerge. Without continuous monitoring, organizations remain blind to these changes.
Modern TPRM approaches focus on identifying and tracking vendors’ externally facing assets, mapping them to risk exposure, and monitoring for vulnerabilities, misconfigurations, and potential initial access points. This allows security teams to detect changes that could indicate early stages of a software supply chain attack.
By combining continuous asset discovery with intelligence-driven risk scoring, organizations can move from reactive vendor assessments to proactive supply chain security—reducing blind spots and strengthening overall resilience.



