Businesses today depend heavily on third-party vendors to handle critical functions, from cloud storage to payment processing. This reliance comes with a price: a growing vulnerability to third-party breaches. For example, the MOVEit Transfer breach exposed sensitive data across multiple organizations due to a single exploited vulnerability. These incidents often lead to significant financial losses, operational downtime, and reputational damage. With the average cost of a data breach reaching $4.88 million globally in 2024, it’s clear that companies cannot afford to ignore the risks posed by their vendors. This article breaks down these costs and explores actionable strategies to mitigate them.
What Are Third-Party Breaches?
Third-party breaches occur when an external vendor, contractor, or partner inadvertently exposes sensitive data or systems to unauthorized access. These breaches often exploit weaknesses in vendor systems, creating a backdoor to the primary organization. In 2024, 68% of breaches involved a human element, emphasizing the widespread nature of these vulnerabilities (Verizon).
Common Causes of Third-Party Breaches
- Human Error: Simple mistakes, such as misconfigured servers or weak passwords, are leading causes of third-party breaches. For example, Stanford reports that 88% of breaches are caused by human error, making it a persistent threat across industries.
- Software Vulnerabilities: Outdated software, insufficient security protocols, and unpatched systems are common entry points for attackers. The MOVEit breach exemplifies this, as attackers exploited a known vulnerability in widely used file transfer software.
- Lack of Oversight: Organizations often fail to thoroughly vet their vendors’ security practices, leading to overlooked risks that attackers can easily exploit.
By understanding these causes and the statistics behind them, businesses can better evaluate and secure their relationships with vendors.
The Financial Costs of Third-Party Breaches
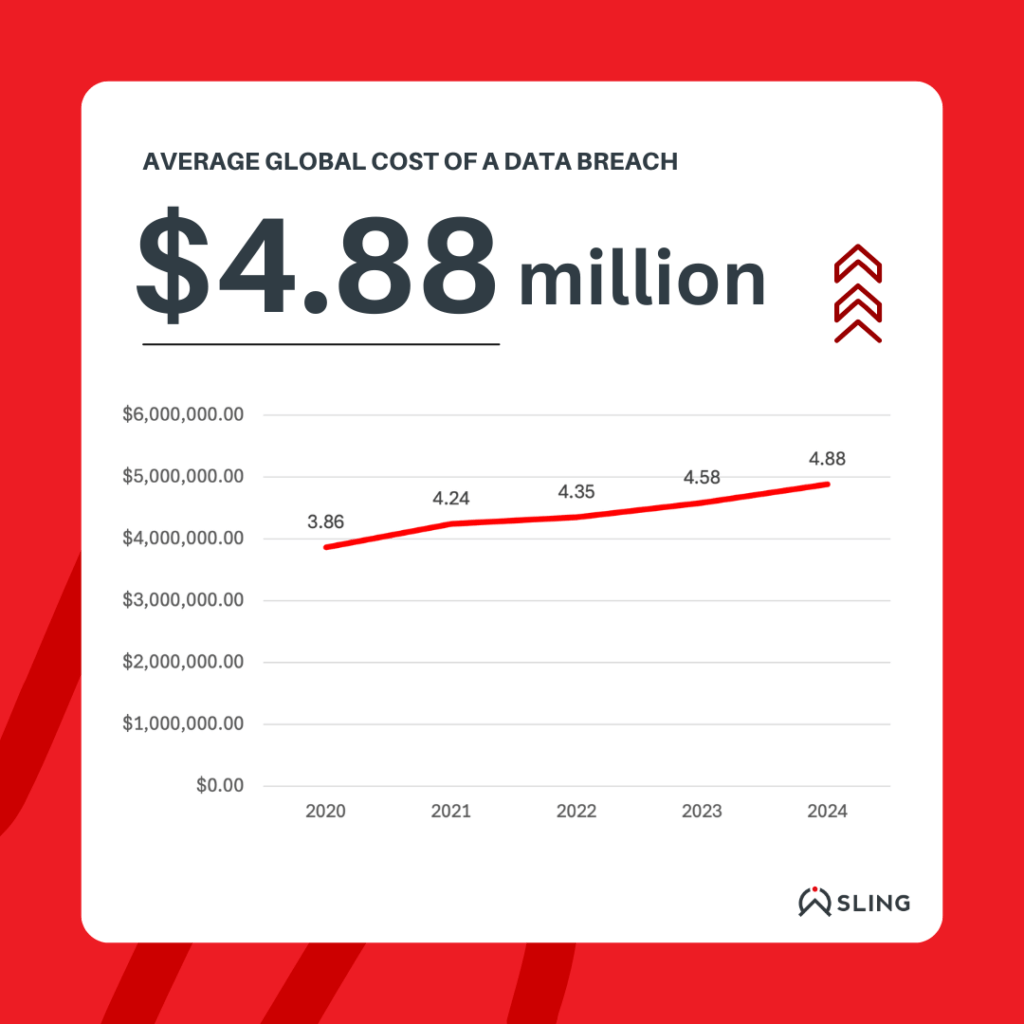
The financial toll of third-party breaches is staggering, with global costs climbing each year. In 2024, the average global cost of a data breach reached $4.88 million, representing a 10% increase over the previous year (IBM). These costs are even higher in specific industries. For example, healthcare organizations face average breach costs of $10.10 million due to the high value of medical data, while financial institutions see average costs of $5.9 million as they grapple with regulatory penalties and fraud prevention measures.
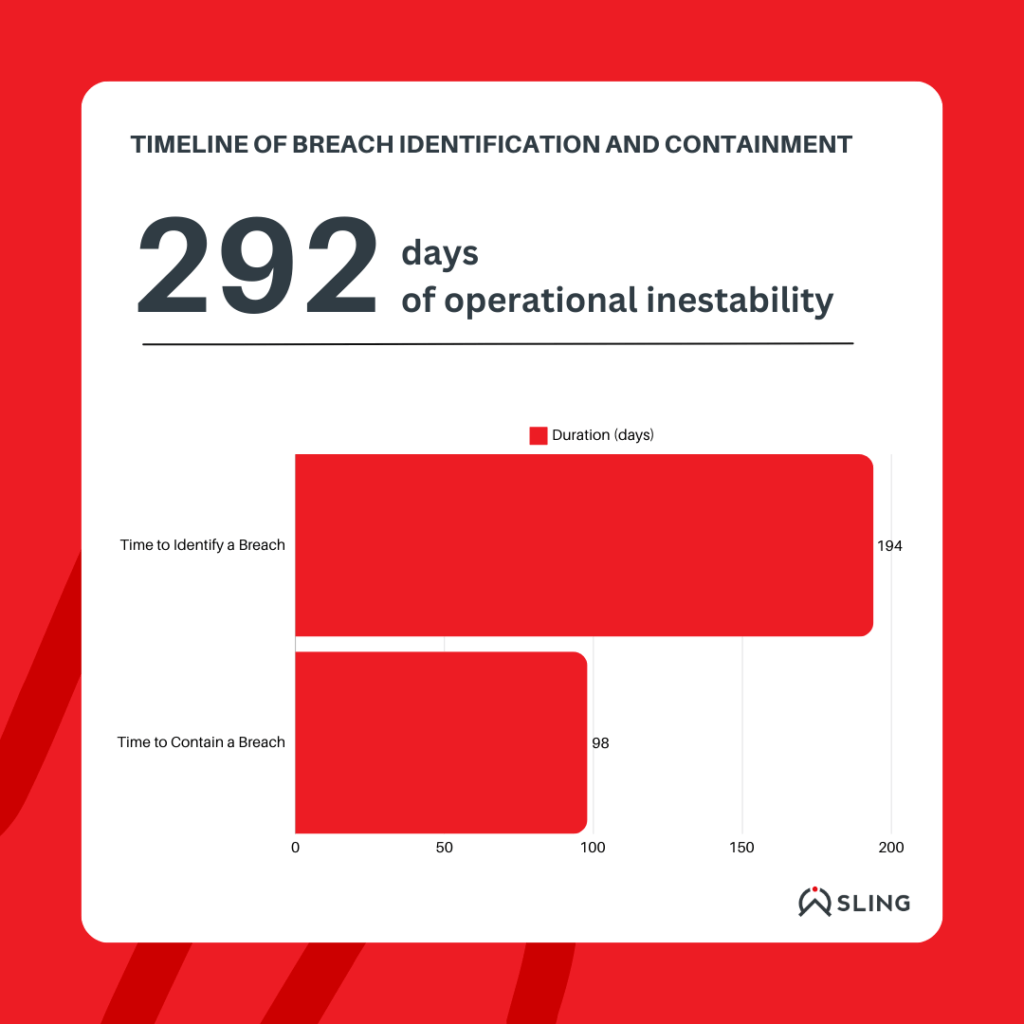
Recovering from ransomware attacks, a growing component of third-party breaches, will cost organizations an average of $2.73 million in 2024 (Sophos). Additionally, the prolonged lifecycle of breaches exacerbates financial losses. On average, it takes 194 days to identify a breach and 292 days to fully contain it (IBM), leading to extended operational disruptions and increased costs.
Third-party breaches, in particular, are significantly more expensive to address than internal breaches. Gartner estimates that remediating a third-party breach costs up to 40% more due to the complexity of managing external relationships and the potential for widespread network impact.
Reputational Damage and Its Long-Term Effects
The impact of third-party breaches extends far beyond immediate financial losses, often leaving a lasting scar on a company’s reputation. Trust is hard-won and easily lost, and data breaches erode the confidence of customers, partners, and stakeholders.
A striking example is the public backlash following the MOVEit breach, where organizations relying on the software faced scrutiny not only for the breach itself but also for their lack of vigilance in vetting vendor security. Studies show that 64% of Americans have never checked if their data was compromised in a breach (Varonis). Yet, breaches still damage brand loyalty as customers feel their trust has been betrayed.
In the aftermath of a breach, companies often experience increased customer churn and declining revenue. This is compounded by the fact that 56% of Americans don’t know what steps to take after their data is exposed, leaving them frustrated and more likely to sever ties with the company. Even well-established brands struggle to recover from the reputational fallout, as rebuilding trust in today’s hyper-connected world is both challenging and time-consuming.
By proactively addressing third-party risks, organizations can better safeguard their reputations and minimize the long-term effects of a breach.
Operational Disruptions
Third-party breaches often cause significant operational disruptions that extend well beyond the initial incident. When a vendor’s systems are compromised, the ripple effects can halt business-critical processes, disrupt service delivery, and create compliance challenges.
For example, during the MOVEit breach, many organizations had to suspend operations to assess the scope of the attack and contain the damage. This downtime resulted in delayed projects, disrupted customer services, and increased costs associated with recovery efforts. On average, it takes 194 days to identify a breach and another 98 days to contain it, meaning businesses could face nearly a year of operational instability (IBM).
Regulatory Compliance
Regulatory compliance is another critical area affected by third-party breaches. Regulations like the GDPR and CCPA impose strict reporting requirements. Additionally, supply-chain regulation guidelines and frameworks, such as DORA, NIS 2, HIPPA, etc. demand strong risk management, and non-compliance can lead to significant fines. Organizations scrambling to meet these requirements during an ongoing breach often face additional penalties and reputational damage.
The Role of Human Error in Third-Party Breaches
Human error plays a significant role in enabling third-party breaches, acting as a gateway for attackers to spread and exploit vulnerabilities. Despite advancements in cybersecurity technology, people remain the weakest link in organizational defenses. Stanford University’s research reveals that 88% of data breaches are directly caused by human error, making it the most persistent risk factor.
Common mistakes include misconfigured systems, weak passwords, and employees falling victim to phishing schemes. In third-party relationships, these errors are magnified. Vendors with inadequate cybersecurity training or poor awareness of threats can unknowingly create vulnerabilities that compromise their clients’ data. For instance, the MOVEit breach exploited a known vulnerability that could have been mitigated with timely patches and better oversight.
In 2024, Verizon’s data showed that 68% of breaches involved a human element, illustrating how widespread this problem is. Even small errors, such as sharing sensitive login credentials over unsecured channels, can lead to catastrophic consequences when attackers gain access to interconnected systems.
Proactive Measures to Mitigate Third-Party Breaches
Mitigating the risks associated with third-party breaches requires a proactive approach to vendor management and cybersecurity practices. Organizations must treat third-party relationships with the same rigor as internal security protocols, ensuring that external partners do not become weak links in their defenses.
Key Strategies for Risk Reduction
- Conduct Regular Vendor Risk Assessments:
Evaluate the security posture of vendors before onboarding and conduct periodic reviews. This includes assessing regulatory compliance with different frameworks like DORA, HIPPA, NIS 2. - Adopt a Zero-Trust Architecture:
Implementing a zero-trust model ensures that no user or system (internal or external) is inherently trusted. Access to critical systems and data should be granted on a need-to-know basis, minimizing the potential impact of a breach. - Develop a Prioritized Plan:
Identify risks and vulnerabilities within the vendor ecosystem and prioritize them based on their potential impact. Addressing the most critical issues first ensures that resources are allocated effectively and vulnerabilities are mitigated before they can be exploited. - Leverage Advanced Monitoring Tools:
Utilize technology to monitor vendor ecosystems for unusual activity and vulnerabilities. Monitoring tools include systems that combine advanced dark net threat intelligence with Attack Surface Management (ASM) for comprehensive oversight.
Lessons from High-Profile Breaches (MOVEit Case Study)
Examining high-profile breaches offers critical insights into the vulnerabilities and consequences associated with third-party risks. One of the most illustrative examples is the MOVEit breach, which serves as a cautionary tale for businesses worldwide.
- Timeline of Events: In 2023, a critical vulnerability in the MOVEit Transfer software was exploited by attackers, compromising sensitive data across multiple organizations. Despite warnings from cybersecurity agencies like the UK’s National Cyber Security Centre (NCSC), many organizations failed to implement patches in time.
- Key Vulnerabilities Exploited: Attackers leveraged unpatched software to gain unauthorized access to highly sensitive information. The exploit highlighted the dangers of relying on third-party tools without continuous oversight and updates.
- Impact: The breach led to widespread operational disruptions, regulatory penalties, and financial losses. Several affected organizations faced significant reputational damage as public confidence plummeted.
Broader Lessons from Third-Party Breaches
- Interconnectivity Increases Risk: Many organizations using MOVEit were unaware of their exposure to vulnerabilities within the software. This lack of visibility underscores the importance of comprehensive vendor risk assessments.
- Speed of Response Matters: Delays in applying patches or addressing vulnerabilities often amplify the impact of breaches. Businesses must prioritize swift action and consistent monitoring.
- Regulatory Ramifications: As seen in the MOVEit case, breaches often lead to investigations and potential penalties under regulations like GDPR or CCPA.



